Is Your Organisation Cyber Resilient for 2026?
Table of Content
Overview
As we are entering 2026, Australia’s cybersecurity landscape is evolving rapidly, and it’s anything but predictable. Enterprises are up against advanced bad actors, fast-growing tech stacks, and soaring regulatory demands.
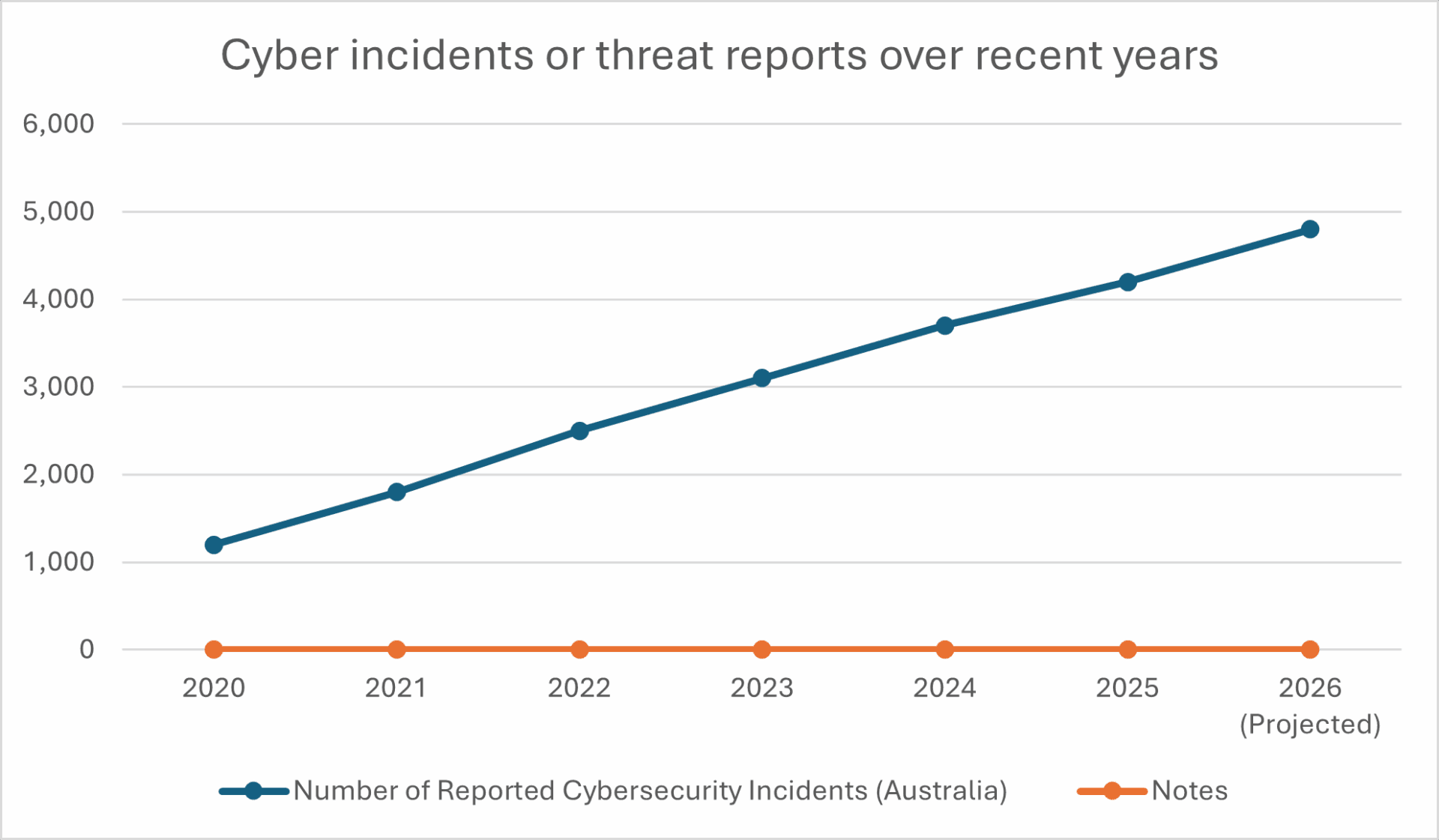
AI-powered attacks are now more than theoretical. Supply-chain attacks are no longer uncommon. Multi-cloud complexity has increased over time. These reasons are driving organisations to consider cybersecurity not only a technical practice, but an integral part of business resilience and governance.
Cybersecurity has now become, quite literally, an issue of trust, continuity, and reputation. Choices that leadership makes ripple out through an organisation and have a real impact on how well (or not) we can manage Incidents.
Cybersecurity Has Become a Leadership Responsibility
For many years, cybersecurity was primarily an IT concern. It was handled by technical teams and security specialists, often isolated from business decision-making. That model is no longer sufficient.
A single breach can disrupt operations, expose sensitive data, and attract regulatory scrutiny within hours. Board members and executives are now expected to understand cyber risk in practical, business-focused terms.
This includes recognising the role of AI, understanding regulatory obligations, and ensuring operational readiness. Cybersecurity decisions are increasingly judged by the quality of leadership oversight, not only by technical controls.
AI-Driven Threats Are Escalating
Artificial intelligence has changed the way cyberattacks are carried out. Threat actors now use AI to automate reconnaissance, generate highly convincing phishing campaigns, and identify system vulnerabilities rapidly.
These attacks scale effortlessly and adapt quickly, often outpacing traditional detection methods. At the same time, many organisations deploy AI internally for security monitoring, analytics, and operational decision-making. While AI can strengthen defences, it also introduces risk if not properly governed. Ethical deployment, accountability, and access control are essential to ensure AI supports security rather than creating new vulnerabilities.
Supply-Chain and Multi-Cloud Risks Continue to Expand
Modern organisations operate in complex ecosystems that include multiple vendors, service providers, and cloud platforms. While these connections enhance efficiency, they also increase exposure to cyber threats.
Supply-chain attacks remain particularly effective because they exploit trust relationships. A compromised vendor can impact multiple organisations before the breach is detected. Multi-cloud environments add another layer of complexity. Different platforms, controls, and visibility gaps increase the likelihood of misconfigurations and security failures.
Organisations that address these risks proactively integrate supply-chain and cloud oversight into their broader risk management programs. Waiting for incidents to reveal weaknesses is no longer a viable strategy.
Identity and Privilege Management Are Critical
As traditional network perimeters dissolve, identity has become the primary security control. Credential theft, insider threats, and privilege abuse are expected to rise further in 2026.
Attackers increasingly rely on valid credentials to gain access, making identity and access management essential. Organisations must implement zero-trust principles, continuously verify users and devices, monitor privileged accounts, and enforce role-based access policies.
Technology alone cannot address these risks. Employee awareness, training, and accountability remain critical to protecting sensitive information.
AI Governance and Ethical Accountability
AI governance is now a business and regulatory expectation. Organisations are required to demonstrate how AI systems operate, how decisions are made, and how risks are controlled.
This applies to AI supporting security operations, customer engagement, or internal processes. Many organisations align AI governance with ISO/IEC 27001 for information security and ISO/IEC 42001 for AI management systems, while referencing Essential Eight, NIST CSF, and Australian regulatory guidance.
Effective governance allows organisations to innovate responsibly while maintaining trust, transparency, and compliance.
Continuous Validation and Proactive Resilience
By 2026, mature organisations will prioritise proactive security over reactive responses. This involves continuously testing, validating, and improving security measures before incidents occur.
Red teaming exercises simulate realistic attacks, vulnerability scanning identifies weaknesses early, and incident response drills improve coordination under pressure. Continuous monitoring ensures both AI-driven and traditional threats remain visible.
Embedding security into day-to-day operations allows organisations to respond quickly and recover effectively, reducing the impact of attacks.
How Risk Associates Supports Organisations
Risk Associates helps organisations strengthen governance, validate security controls, and measure cybersecurity maturity. The focus is on sustained preparedness rather than reactive fixes.
Key support areas include:
| Area | Focus | Outcome |
|---|---|---|
| AI Governance | Ethical deployment, accountability, compliance | Secure, auditable AI systems |
| Risk Assessments | Red Teaming, vulnerability scans, multi-cloud audits | Early detection and remediation |
| Compliance & Certification | ISO/IEC 27001, ISO/IEC 42001, NIST CSF, Essential Eight | Regulatory alignment and operational confidence |
Independent assessment provides clarity, confidence, and evidence for both internal stakeholders and external partners.
Building Cyber Resilience for 2026
The cybersecurity landscape in Australia will be shaped by rapid AI adoption, complex threat models, and growing expectations around governance and ethics. Organisations that continue to rely on reactive measures risk remaining exposed, while those that embed resilience, compliance, and accountability into their operating model will adapt and respond effectively.
Cybersecurity is no longer only about protection. It is about trust, operational continuity, and long-term confidence. Risk Associates continues to support organisations through practical guidance, structured assurance, and clear pathways toward sustainable cyber resilience.
